Ian Birdsey: WannaCry attack a wake-up call for business
This article contains affiliate links. We may earn a small commission on items purchased through this article, but that does not affect our editorial judgement.
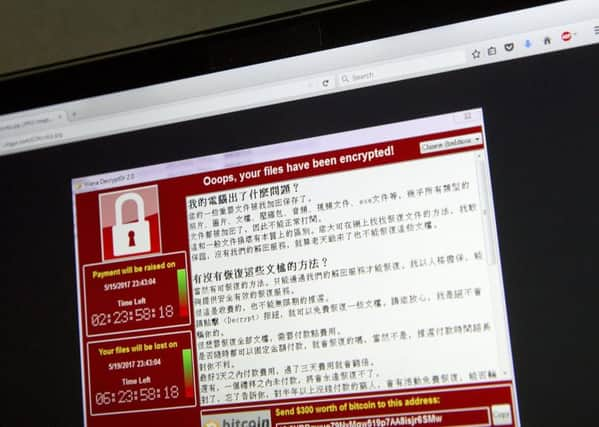

Ransomware is a type of cyber attack that sees hackers install malicious software on to computer systems that prevent businesses carrying out everyday operations or accessing data or other assets. Businesses are prompted to make a payment to the hackers to decrypt data encrypted by the attack – and sometimes even offer a helpline service on how payment should be made.
Advertisement
Hide AdAdvertisement
Hide AdThe cyber attack, described by Interpol as unprecedented in scale and which sought ransom payments valued at $300 (£230) and then $600 in the cryptocurrency bitcoin, should alert organisations that they face a crippling impact to their operations if they fail to take basic measures to protect the security of critical systems and data. The malicious ransomware spread to systems that were running on out-of-date software that contained a vulnerability, despite a security update for the software being available since 14 March.
The WannaCry ransomware attack appears to have operated like a worm attack that was common in the early 2000s by searching for and spreading to systems that contained a particular security vulnerability. The attack does not appear to have been particularly sophisticated, and indeed the UK’s National Cyber Security Centre has indicated that the most basic cybersecurity hygiene by organisations – keeping security patches up-to-date, running antivirus programs and backing up data – would have been sufficient to repel this attack.
The scale of the WannaCry attack shows that many organisations are not treating the cyber threats they face seriously enough. There is an opportunity for the UK, and other countries across the EU, to drive better practices when they come to implement the EU’s Network and Information Security (NIS) Directive. This sets out measures designed to ensure critical IT systems in central sectors of the economy like banking, energy, health and transport are secure.
The directive will apply to operators of “essential services” and “digital service providers” and EU countries have until 9 May 2018 to incorporate the measures in to national law. Under the Directive, each EU country will be responsible for determining its own “effective, proportionate and dissuasive” penalties for infringement of the NIS rules. However, possible penalties could include fines, public naming of those in breach, and/or a requirement to rectify deficiencies identified with cybersecurity measures deployed.
• READ MORE: Fraser Nicol: A timely reminder on ransomware risks
The cyber risk faced is particularly pronounced in areas of infrastructure that are critical to everyday life, such as banking, health, energy and transport – all the sectors within the scope of the NIS Directive.
Advertisement
Hide AdAdvertisement
Hide AdCyber risk has risen up the boardroom agenda in recent times, but it is clear that, despite a raft of new legislation, government guidance and industry warnings, many organisations are still vulnerable to attack. Organisations of all types and sizes should check whether their anti-virus programmes are operating effectively, whether they are up-to-date with their security patching for software and ensure they back-up data onto systems that are operationally distinct from the main systems they rely on, to ensure that systems can be switched and operations restored quickly in the event a ransomware attack hitting.
In addition, organisations should put in place, and test, an incident response plan. It would enable them to efficiently manage any breach they experience with the help of third party experts, such as forensic IT investigators, PR agencies and legal advisors, in line with their legal and regulatory obligations.
• Ian Birdsey is a partner and expert in data protection and cyber issues at legal firm Pinsent Masons